Bypassing ASLR in Windows 10 - Free download as PDF File (.pdf), Text File (.txt) or view presentation slides online. Windows 10 ASLR Bypass. How to Enable ASLR in Windows Defender. Step 1: Type in notepad in the taskbar search field and press Enter. Here, create a first blank text script by entering the following text –. Step 2: After you copy the entire text into Notepad, click File at the top, and from the submenu, choose Save as. Address space layout randomization (ASLR) is a computer security technique involved in preventing exploitation of memory corruption vulnerabilities. In order to prevent an attacker from reliably jumping to, for example, a particular exploited function in memory, ASLR randomly arranges the address space positions of key data areas of a process.
A Carnegie-Mellon CERT researcher has discovered that Microsoft broke some use-cases for its Address Space Layout Randomisation (ASLR) mechanism, designed to severely hamper hackers' attempts to exploit security bugs.
The programming blunder is simple: as of Windows 8, a flaw in Microsoft's system-wide mandatory ASLR implementation meant applications were allocated addresses with zero entropy – in other words, where they were placed in memory was supposed to be randomized, but wasn't. Windows 10 suffers from the same problem, too.
It means return-oriented programming (ROP) attack code written to exploit vulnerabilities have a much, much higher chance of working and successfully infecting a system than previously expected.
The bug was found by CERT/CC analyst Will Dormann, and was published late last week, here.
Dormann was researching why Microsoft's equation editor opened Excel to remote code execution (fixed in last week's patch Tuesday list) when he discovered the ASLR slip-up.

Here's the summary of the bug:
Microsoft Windows 8 introduced a change in how system-wide mandatory ASLR is implemented. This change requires system-wide bottom-up ASLR to be enabled for mandatory ASLR to receive entropy. Tools that enable system-wide ASLR without also setting bottom-up ASLR will fail to properly randomise executables that do not opt in to ASLR.
It's important to note that while bad, the bug only affects a subset of applications:
- Applications forced to used ASLR, via a mandatory system-wide policy, are affected;
- Applications that opt into ASLR aren't affected;
- Applications that never used ASLR aren't affected either way, of course.
Essentially, system-wide mandatory ASLR requires a feature called system-wide bottom-up ASLR to be enabled. Unfortunately, Windows Defender Exploit Guard nor the deprecated Enhanced Mitigation Experience Toolkit (EMET) don't switch on that latter part, thus derailing the forced ASLR. Exploit Guard can enable bottom-up ASLR, but doesn't from the user interface – you have to have to prod around in the registry to flip the switch:
Both EMET and Windows Defender Exploit Guard enable system-wide ASLR without also enabling system-wide bottom-up ASLR. Although Windows Defender Exploit guard does have a system-wide option for system-wide bottom-up-ASLR, the default GUI value of 'On by default' does not reflect the underlying registry value (unset). This causes programs without /DYNAMICBASE to get relocated, but without any entropy. The result of this is that such programs will be relocated, but to the same address every time across reboots and even across different systems.
As Dormann tweeted:
Actually, with Windows 7 and EMET System-wide ASLR, the loaded address for eqnedt32.exe is different on every reboot. But with Windows 10 with either EMET or WDEG, the base for eqnedt32.exe is 0x10000 EVERY TIME.
Conclusion: Win10 cannot be enforce ASLR as well as Win7! pic.twitter.com/Jp10nqk1NQ
Or for those not proficient in setting bits in binary registry values (such as myself), either manually set the values indicated in this picture, or if you don't care about clobbering any existing system-wide mitigations, import this .REG file:https://t.co/nOnhvU2xZFpic.twitter.com/i4YNpET0wq Elementos del estilo tipografico robert bringhurst pdf download.
— Will Dormann (@wdormann) November 16, 2017As Dormann's tweet – and his Gist post – describe, sysadmins can set a registry value to force bottom-up ASLR, a wonderful task if you're in charge of a fleet of machines. So far, Microsoft hasn't published any fix. ®
 -->
-->Applies to:
Want to experience Defender for Endpoint? Sign up for a free trial.
Exploit protection automatically applies a number of exploit mitigation techniques on both the operating system processes and on individual apps.
Configure these settings using the Windows Security app on an individual device. Then, export the configuration as an XML file so you can deploy to other devices. Use Group Policy to distribute the XML file to multiple devices at once. You can also configure the mitigations with PowerShell.
This article lists each of the mitigations available in exploit protection. It indicates whether the mitigation can be applied system-wide or to individual apps, and provides a brief description of how the mitigation works.
It also describes how to enable or configure the mitigations using Windows Security, PowerShell, and mobile device management (MDM) configuration service providers (CSPs). This is the first step in creating a configuration that you can deploy across your network. The next step involves generating, exporting, importing, and deploying the configuration to multiple devices.
Warning
Some security mitigation technologies may have compatibility issues with some applications. You should test exploit protection in all target use scenarios by using audit mode before deploying the configuration across a production environment or the rest of your network.
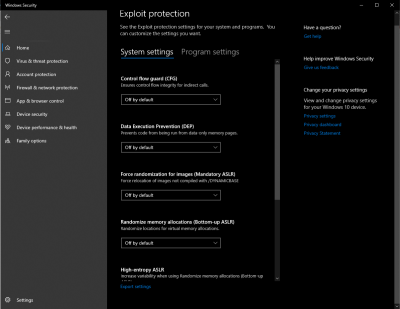
Exploit protection mitigations
All mitigations can be configured for individual apps. Some mitigations can also be applied at the operating system level.
You can set each of the mitigations on, off, or to their default value. Some mitigations have additional options that are indicated in the description in the table.
Default values are always specified in brackets at the Use default option for each mitigation. In the following example, the default for Data Execution Prevention is 'On'.
The Use default configuration for each of the mitigation settings indicates our recommendation for a base level of protection for everyday usage for home users. Enterprise deployments should consider the protection required for their individual needs and may need to modify configuration away from the defaults.
For the associated PowerShell cmdlets for each mitigation, see the PowerShell reference table at the bottom of this article.
| Mitigation | Description | Can be applied to | Audit mode available | |
|---|---|---|---|---|
| Control flow guard (CFG) | Ensures control flow integrity for indirect calls. Can optionally suppress exports and use strict CFG. | System and app-level | No | |
| Data Execution Prevention (DEP) | Prevents code from being run fromt allow child processes | Prevents an app from creating child processes. | App-level only | Yes |
| Export address filtering (EAF) | Detects dangerous operations being resolved by malicious code. Can optionally validate access by modules commonly used by exploits. | App-level only | Yes | |
| Import address filtering (IAF) | Detects dangerous operations being resolved by malicious code. | App-level only | Yes | |
| Simulate execution (SimExec) | Ensures that calls to sensitive APIs return to legitimate callers. Only configurable for 32-bit (x86) applications. Not compatible with ACG. | App-level only | Yes | |
| Validate API invocation (CallerCheck) | Ensures that sensitive APIs are invoked by legitimate callers. Only configurable for 32-bit (x86) applications. Not compatible with ACG | App-level only | Yes | |
| Validate handle usage | Causes an exception to be raised on any invalid handle references. | App-level only | No | |
| Validate image dependency integrity | Enforces code signing for Windows image dependency loading. | App-level only | No | |
| Validate stack integrity (StackPivot) | Ensures that the stack hasn't been redirected for sensitive APIs. Not compatible with ACG. | App-level only | Yes |
Important
If you add an app to the Program settings section and configure individual mitigation settings there, they will be honored above the configuration for the same mitigations specified in the System settings section. The following matrix and examples help to illustrate how defaults work:
| Enabled in Program settings | Enabled in System settings | Behavior |
|---|---|---|
| Yes | No | As defined in Program settings |
| Yes | Yes | As defined in Program settings |
| No | Yes | As defined in System settings |
| No | Yes | Default as defined in Use default option |
Example 1
Mikael configures Data Execution Prevention (DEP) in the System settings section to be Off by default.
Mikael then adds the app test.exe to the Program settings How to reset the password for superset on mac. section. In the options for that app, under Data Execution Prevention (DEP), he enables the Override system settings option and sets the switch to On. There are no other apps listed in the Program settings section.
The result will be that DEP only will be enabled for test.exe. All other apps will not have DEP applied.
Example 2
Josie configures Data Execution Prevention (DEP) in the System settings section to be Off by default.
Josie then adds the app test.exe to the Program settings section. In the options for that app, under Data Execution Prevention (DEP), she enables the Override system settings option and sets the switch to On.
Josie also adds the app miles.exe to the Program settings section and configures Control flow guard (CFG) to On. She doesn't enable the Override system settings option for DEP or any other mitigations for that app.
The result will be that DEP will be enabled for test.exe. DEP will not be enabled for any other app, including miles.exe. CFG will be enabled for miles.exe.
Note
If you have found any issues in this article, you can report it directly to a Windows Server/Windows Client partner or use the Microsoft technical support numbers for your country.
Configure system-level mitigations with the Windows Security app
Open the Windows Security app by selecting the shield icon in the task bar or searching the start menu for Defender.
Select the App & browser control tile (or the app icon on the left menu bar) and then select Exploit protection.
Under the System settings section, find the mitigation you want to configure and select one of the following. Apps that aren't configured individually in the Program settings section will use the settings configured here:
- On by default - The mitigation is enabled for apps that don't have this mitigation set in the app-specific Program settings section
- Off by default - The mitigation is disabled for apps that don't have this mitigation set in the app-specific Program settings section
- Use default - The mitigation is either enabled or disabled, depending on the default configuration that is set up by Windows 10 installation; the default value (On or Off) is always specified next to the Use default label for each mitigation
Note
You may see a User Account Control window when changing some settings. Enter administrator credentials to apply the setting.
Changing some settings may require a restart.
Repeat this for all the system-level mitigations you want to configure.
Go to the Program settings section and choose the app you want to apply mitigations to:
- If the app you want to configure is already listed, select it and then select Edit
- If the app isn't listed, at the top of the list select Add program to customize and then choose how you want to add the app:
- Use Add by program name to have the mitigation applied to any running process with that name. You must specify a file with an extension. You can enter a full path to limit the mitigation to only the app with that name in that location.
- Use Choose exact file path to use a standard Windows Explorer file picker window to find and select the file you want.
After selecting the app, you'll see a list of all the mitigations that can be applied. To enable the mitigation, select the check box and then change the slider to On. Select any additional options. Choosing Audit will apply the mitigation in audit mode only. You will be notified if you need to restart the process or app, or if you need to restart Windows.
Repeat these steps for all the apps and mitigations you want to configure. Select Apply when you're done setting up your configuration.
You can now export these settings as an XML file or continue on to configure app-specific mitigations.
Exporting the configuration as an XML file allows you to copy the configuration from one device onto other devices.
PowerShell reference
You can use the Windows Security app to configure Exploit protection, or you can use PowerShell cmdlets.
The configuration settings that were most recently modified will always be applied - regardless of whether you use PowerShell or Windows Security. This means that if you use the app to configure a mitigation, then use PowerShell to configure the same mitigation, the app will update to show the changes you made with PowerShell. If you were to then use the app to change the mitigation again, that change would apply.
Important
Any changes that are deployed to a device through Group Policy will override the local configuration. When setting up an initial configuration, use a device that will not have a Group Policy configuration applied to ensure your changes aren't overridden.
You can use the PowerShell verb Get or Set with the cmdlet ProcessMitigation. Using Get will list the current configuration status of any mitigations that have been enabled on the device - add the -Name cmdlet and app exe to see mitigations for just that app:
Important
System-level mitigations that have not been configured will show a status of NOTSET.
For system-level settings, NOTSET indicates the default setting for that mitigation has been applied.
For app-level settings, NOTSET indicates the system-level setting for the mitigation will be applied.
The default setting for each system-level mitigation can be seen in the Windows Security.
Use Set to configure each mitigation in the following format:
Where:
Disable Aslr Windows 10 Registry
- <Scope>:
-Nameto indicate the mitigations should be applied to a specific app. Specify the app's executable after this flag.-Systemto indicate the mitigation should be applied at the system level
- <Action>:
-Enableto enable the mitigation-Disableto disable the mitigation
- <Mitigation>:
- The mitigation's cmdlet as defined in the mitigation cmdlets table below, along with any suboptions (surrounded with spaces). Each mitigation is separated with a comma.
For example, to enable the Data Execution Prevention (DEP) mitigation with ATL thunk emulation and for an executable called testing.exe in the folder C:AppsLOBtests, and to prevent that executable from creating child processes, you'd use the following command:
Important
Separate each mitigation option with commas.
If you wanted to apply DEP at the system level, you'd use the following command:
To disable mitigations, you can replace -Enable with -Disable. However, for app-level mitigations, this will force the mitigation to be disabled only for that app.
If you need to restore the mitigation back to the system default, you need to include the -Remove cmdlet as well, as in the following example:
Hauppauge wintv v8 serial kygen. You can also set some mitigations to audit mode. Instead of using the PowerShell cmdlet for the mitigation, use the Audit mode cmdlet as specified in the mitigation cmdlets table below.
For example, to enable Arbitrary Code Guard (ACG) in audit mode for the testing.exe used previously, you'd use the following command:
You can disable audit mode by using the same command but replacing -Enable with -Disable.
PowerShell reference table
Disable Aslr Windows 10 Settings
_013.png)
This table lists the PowerShell cmdlets (and associated audit mode cmdlet) that can be used to configure each mitigation.
| Mitigation | Applies to | PowerShell cmdlets | Audit mode cmdlet |
|---|---|---|---|
| Control flow guard (CFG) | System and app-level | CFG, StrictCFG, SuppressExports | Audit not available |
| Data Execution Prevention (DEP) | System and app-level | DEP, EmulateAtlThunks | Audit not available |
| Force randomization for images (Mandatory ASLR) | System and app-level | ForceRelocateImages | Audit not available |
| Randomize memory allocations (Bottom-Up ASLR) | System and app-level | BottomUp, HighEntropy | Audit not available |
| Validate exception chains (SEHOP) | System and app-level | SEHOP, SEHOPTelemetry | Audit not available |
| Validate heap integrity | System and app-level | TerminateOnError | Audit not available |
| Arbitrary code guard (ACG) | App-level only | DynamicCode | AuditDynamicCode |
| Block low integrity images | App-level only | BlockLowLabel | AuditImageLoad |
| Block remote images | App-level only | BlockRemoteImages | Audit not available |
| Block untrusted fonts | App-level only | DisableNonSystemFonts | AuditFont, FontAuditOnly |
| Code integrity guard | App-level only | BlockNonMicrosoftSigned, AllowStoreSigned | AuditMicrosoftSigned, AuditStoreSigned |
| Disable extension points | App-level only | ExtensionPoint | Audit not available |
| Disable Win32k system calls | App-level only | DisableWin32kSystemCalls | AuditSystemCall |
| Do not allow child processes | App-level only | DisallowChildProcessCreation | AuditChildProcess |
| Export address filtering (EAF) | App-level only | EnableExportAddressFilterPlus, EnableExportAddressFilter [1] | Audit not available[2] |
| Import address filtering (IAF) | App-level only | EnableImportAddressFilter | Audit not available[2] |
| Simulate execution (SimExec) | App-level only | EnableRopSimExec | Audit not available[2] |
| Validate API invocation (CallerCheck) | App-level only | EnableRopCallerCheck | Audit not available[2] |
| Validate handle usage | App-level only | StrictHandle | Audit not available |
| Validate image dependency integrity | App-level only | EnforceModuleDepencySigning | Audit not available |
| Validate stack integrity (StackPivot) | App-level only | EnableRopStackPivot | Audit not available[2] |
Windows 10 Free Upgrade
[1]: Use the following format to enable EAF modules for dlls for a process:
[2]: Audit for this mitigation is not available via PowerShell cmdlets.
Customize the notification
Remove Aslr Windows 10
For more information about customizing the notification when a rule is triggered and blocks an app or file, see Windows Security.